
Domain - AWS
Objective After viewing how we can deploy our own EC2 instance to then incorporate our Docker containers on it, it is time for us to purchase a real domain with AWS and configure it as we want. T...

Objective After viewing how we can deploy our own EC2 instance to then incorporate our Docker containers on it, it is time for us to purchase a real domain with AWS and configure it as we want. T...
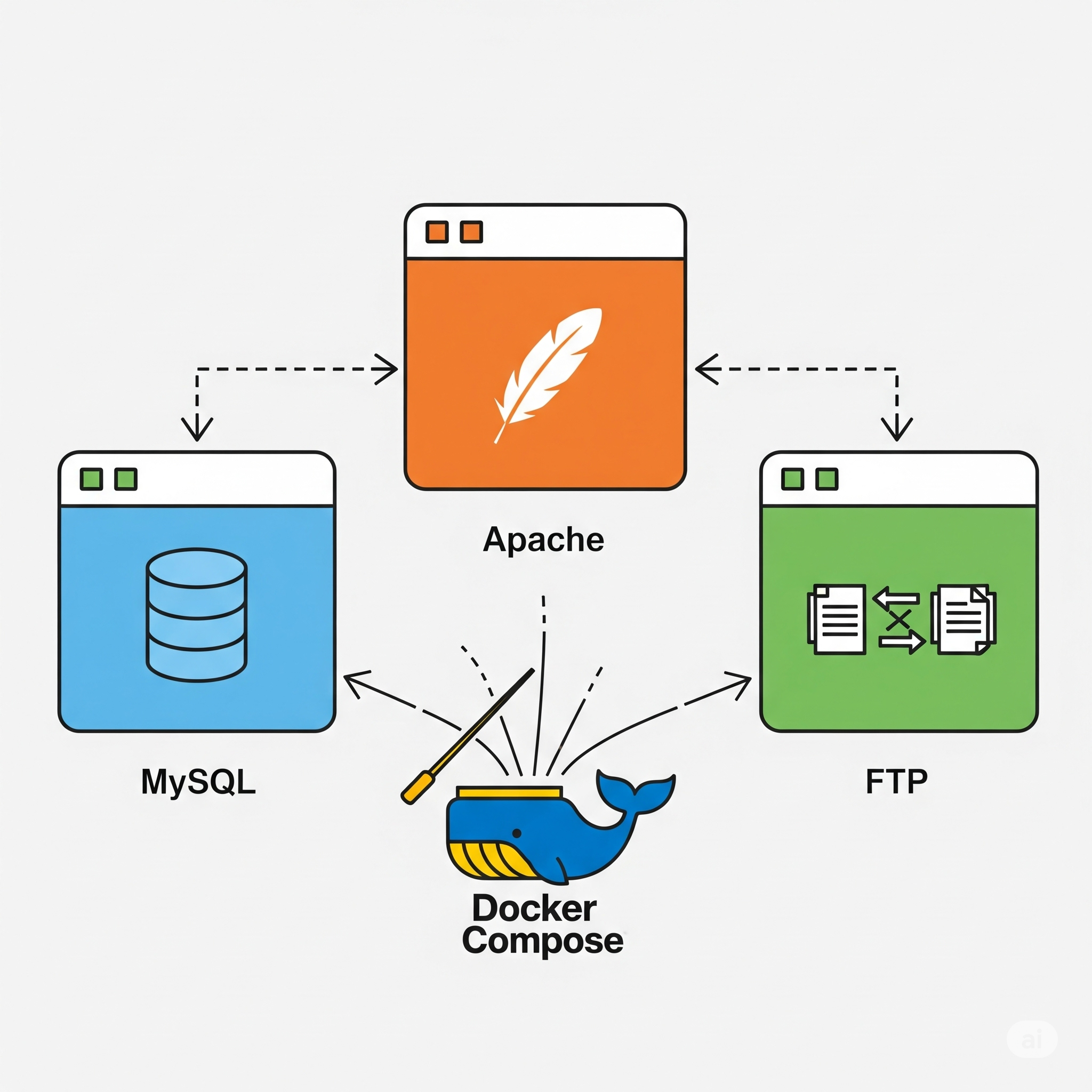
Objective It is time to integrate all the containers we’ve configured so far. Today, I will be explaining what Docker Compose is and show you the advantages it has when it comes to creating and ma...

Objective Today I will be explaining how to configure a MySQL database and how to connect it to our web application. I will also introduce a code flaw on purpose to show how lack of input validati...

Objective The goal here is to configure a web server (Apache in this case) inside a Docker container. This will have a login form which requires some user credentials which will be linked to a MyS...

Objective My goal is to create a realistically configured FTP server that will become the initial point of compromise in our upcoming chained exploit demonstration. Building the Foothold To kick ...

Foothold As is common in real life pentests, you will start the Puppy box with credentials for the following account: Username: levi.james Password: KingofAkron2025! Nmap Scan PORT STATE S...